Network Security Groups and Firewall
In AWS, a security group controls the traffic that is allowed to reach or leave the resources that is associated with. You can associate a security group with an EC2 instance to regulate:
- Access to ports
- Authorised IP ranges - IPv4 and IPv6
- Control of inbound network (from other to the instance)
- Control of outbound network (from the instance to other)
Security groups only contains allow rules, they can referenced by IP addresses or by security group.
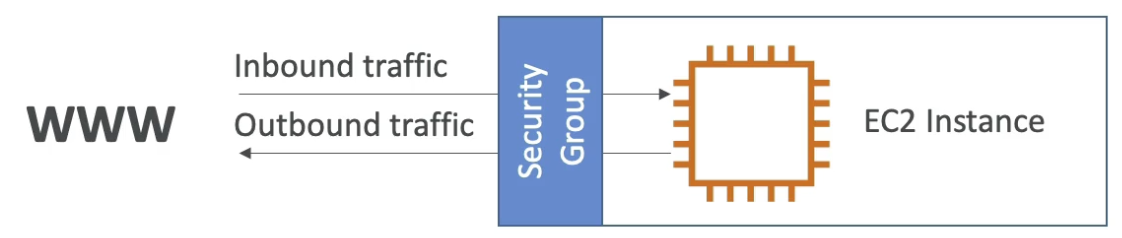
Properties of security groups
- Can be attached to multiple instances, an instance can have multiple security groups.
- You can make communication between instances under control by associating them security groups.
- Locked down to a region/VPC combination, if you switched to another region, you have to create new security group.
- If your application is not accessible (time out), there is a security group rule restriction on it.
- If your application gives a “connection refused” error, then it’s an application error or it’s not launched.
- All inbound traffic is blocked by default.
- All outbound traffic is authorised by default.
- It is a good practice to maintain one separate security group for SSH access.
IAM roles in EC2
To allow the EC2 instances to access your other cloud resources and data, they need to be assigned with certain IAM roles to grant them necessary credentials. You can create IAM roles from the IAM console and assigned some specific roles as per the need to the EC2 instances.
Back to parent node: Cloud Computing
Cloud_computing AWS AWS_CLF-C02 EC2 AWS_security Security_groups Firewall
Reference - Udemy Ultimate AWS Certified Cloud Practitioner CLF-C02