Public-key cryptography also known as asymmetric cryptography, it is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Different from symmetric cryptography, which both sides share the same key or secret code, asymmetric cryptography eliminates the challenge of securely sharing the common keys, allowing encryption with one key and decryption with the other. The asymmetric cryptography concept is also used in Digital Signature.
How does the key pair work
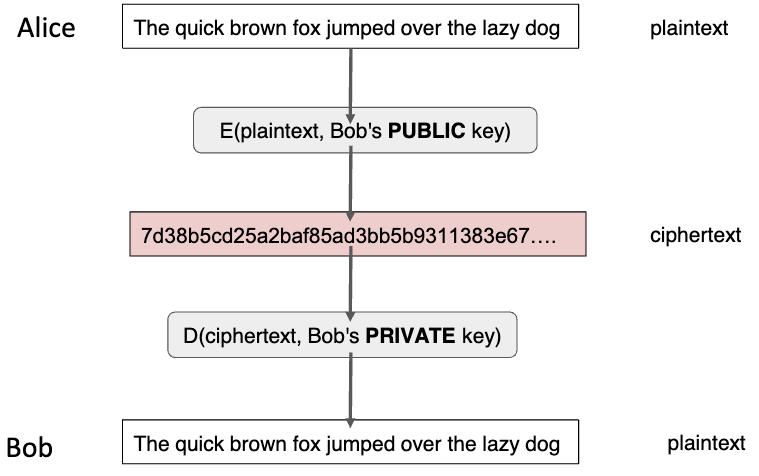
Alice wants to send Bob a message. Bob knows a private key (KPRIV,Bob) and a related but different public key (KPUB,Bob)
- Receiver Bob public key announcement
- Bob announces his public key (KPUB,Bob) to the public, including Alice. This can be done openly, such as on a web page or in a public key repository.
- Encryption by sender Alice
- Alice wants to send a confidential message (m) to Bob.
- To encrypt the message, Alice uses an encryption algorithm (E) and Bob’s public key (KPUB,Bob)
- The encryption process results in cipher text (c)
- The cipher text c where c = E(m, KPUB,Bob)
- Decryption by Bob
- Bob uses a decryption algorithm (D) with his private key to decrypt the message.
- The decryption process can be description in mathematical terms
- D(E(m, KPUB,Bob), KPRIV,Bob) = m
Note
The message sender Alice doesn’t need any secrete information. To send a confidential message to Bob. The public key of receiver Bob and the encryption algorithm are known to everyone. (Kerckhoffs principle).
The important security feature of asymmetric cryptography is that the private key should be computationally infeasible to compute from just the public key. (Trapdoor properties).
Public key cryptography application
| Algorithm | Encryption/Decryption | Digital Signature | Key Exchange |
|---|---|---|---|
| RSA Algorithm | Yes | Yes | Yes |
| Diffe-Hellman | No | No | Yes |
| Elliptic Curve | Yes | Yes | Yes |
| DSS | No | Yes | No |
Security of public keys
How can we protect the information about Bob’s public keys from attack, and get it securely to Alice?
- If attackers can changes the website where Bob’s public key is stored, and put a different value there.
- Attackers could then read messages intended for Bob
- Attackers could prevent Bob reading messages intended for him (denial of service)
To prevent this, Bob can prove his identity to a mutually trusted third party, who issues a Digital Certificate that links Bob’s public key with their statement that they have been convinced of Bob’s identity.
Back to parent page: Network Security and Cryptography
Computer_networks Network_security Key_pair Public_key Private_key INFO1112 #Digital_certificate Asymmetric_cryptography Certificate_Authority