Software Access control
Access control is specified in the security policy aimed at controlling access to resources and assets. It determines who can access what resources and under what condition. Access control includes authentication (process of acquiring evidence of the identity of another party) and authorisation (the allocation of a privilege to a party).
Operating system access control
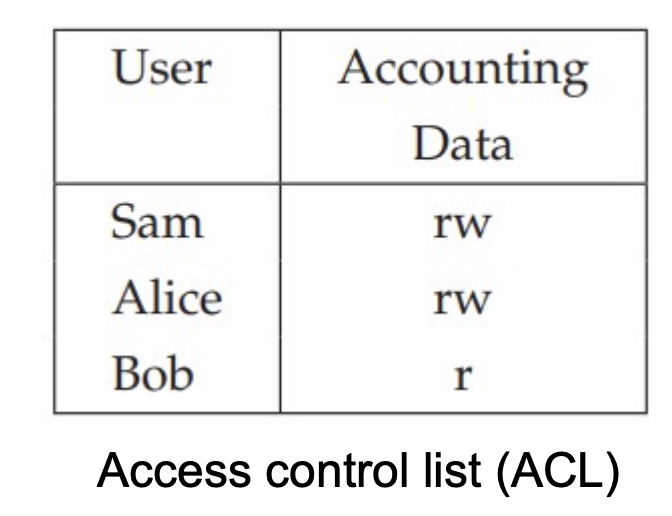
Access Control Lists (ACLs)
ACLs define the access of subjects to objects. They are used to control access to files, directories, network devices, and more. Entry in ACL user ID with a mapping to operations, operations can be coarse (read/write/execute) or very fine-grained.
ACLs are common in all UNIX systems also exist in Windows.
 You can learn more about file permissions and manipulate permissions using Bash command in File Permission.
You can learn more about file permissions and manipulate permissions using Bash command in File Permission.
Special permissions
Special permissions make up a four access levels in addition to user, group, and other. Special permissions allow for additional privileges over the standard permission sets.
SUID
User + S (pecial) is commonly denoted as SUID, the special permission allows a file with SUID aways executes as the user who owns the file, regardless of the user passing the command.
Take below as an example.
$ ls -l /usr/bin/passwd
-rwsr-xr-x. 1 root root 33544 Dec 13 2019 /usr/bin/passwd
- The first
-means it is a regular file (not a directory, symbolic link, or special file). - The following three letters are owner permissions:
rwsr: The owner has read accessw: The owner has write accesss: The owner has setuid permission, indicated by thesin place of the usual execute (x) bit. This means when this file is executed, it will run with the privileges of its owner, regardless of who runs it.
SGID
Group + S (pecial) is denoted as GUID. If it sets on a file, it allows the file to be executed as the group that owns the file (similar to SUID). If set on a directory, any files created in the directory will have their group ownership set to that of the directory owner.
$ ls -l
total 0
drwxrws---. 2 tcarrigan tcarrigan 69 Apr 7 11:31 my_articles
- The first
dmeans it is a directory. - In the group permission bits, they specifies the permissions for the group that owns the directory:
rwsr: The group members have read permissions.w: The group members have write permissions.s: The setgid bit is set, represented bysinstead ofx. This means files created in this directory will inherit the group ownership of the directory. If this were a regular executable file, it would run with the group privileges of the file owner.
Sticky bit
The sticky bit is a special permission that primarily used on directory to control the deletion or renaming of files within that directory. When a sticky bit is set on a directory, only the owner of the file, owner of the directory, or the root user can delete or rename files within that directory, regardless of the write permissions.
$ ls -l
total 0
drwxrwxrwt. 2 tcarrigan tcarrigan 69 Apr 7 11:33 my_articles
The sticky bit is represented by a t in the execute position for “others”.
Unix system access control
Each user has a UserID (UID) and a GroupID (GID).
Two forms of access control - DAC and MAC
Discretionary Access Control (DAC) Discretionary Access Control (DAC), the resource owner decides who can access their resources. This model offers flexibility and is commonly used in enterprise environments where collaboration is essential.
Mandatory Access Control (MAC) Mandatory Access Control (MAC) uses a centralised authority to enforce strict access polices. It is highly secure and often used in government and military settings where data sensitivity is critical.
Access control methods
Sandbox
Sandbox is a shielded environment where malicious applications cannot interfere with the surrounding environment. It typically provides a limited API to interact with.
For example, Google Chrome runs each tab in their own process.
Virtualisation
Virtual Machines (VMs) emulate a compute system, provide isolated environments. They allow to run software even if the real environment it was written for is not available. Virtualisation technology is not designed for access control, but the typically high effort required to break out raises the bar for attackers. However, vulnerabilities in hypervisors (e.g. software managing VMs) can be exploited. Keeping hypervisors up-to-date is crucial.
Docker
Docker uses similar technology than VMs (more in Containerisation VS virtualisation). In docker, app cannot communicate with app in another container. However, the docker daemon is a critical component and should be secured to prevent unauthorised access. Docker relies on the Linux kernel’s namespace and control groups to provide isolation and resource management, any user who can start/stop containers can interact with the daemon. (attack surface)
Middleware access control
Middleware can either be on the same host (same machine or environment) or distributed (spread across multiple systems). Middleware like Advanced Message Queuing Protocol (AMQP) handles communication and data exchange between systems; Remote Procedure Calls (RPCs) that allows systems to communicate by making procedure calls over the network, enable distributed systems to interact as if they were local. Middleware can be complex due to its distributed nature and interaction of many components. Therefore, requires find-grained access controls. Middleware often manages multiple services, so permissions must be clearly defined to ensure only authorised users have access and protect it from external access.
Database access control
Modern Database Management Systems (DBMSes) are designed to handle multiple users and processes simultaneously. This requires access control to ensure that users only interact with data they are authorised to access by using authentication upon database connection (e.g. username and password). Once authenticated, the DBMS has its own internal privilege management to enforce access control (i.e. read, write, execute specific queries).
SQL standard for access control
The SQL standard for access control defines methods for implementing fine-grained access control, meaning that permissions can be defined at very specific levels (e.g. allowing a user to access only specific columns or rows within a table).
Necessity of OS protections
Even though a DBMS control access to the database, the actual data is stored either on disk or RAM. This means that the operating system still plays a crucial role in protecting underlying data. Such as file permissions, memory protection (which will be mentioned later) to secure physical storage of the data. DBMSes often map users from the OS to roles within the database. These roles define the specific actions or queries a user can perform. (e.g. an OS system admin user might be mapped to a high-privileged DB role).
Integrity controls
Many DBMSes include mechanisms for ensuring data integrity, such as constraints (e.g. unique, foreign key constraints) that ensure data consistency. These controls are essential but can be computationally expensive to enforce, especially in large systems with lots of transactions.
Browser access control
Web browsers can be thought of as middleware, facilitating interactions between users, web servers, and applications. Just like other middleware systems, they need access control to ensure that only authorised actions are performed and that data is not exposed or manipulated by unauthorised scripts or sites.
Same-Origin Policy (SOP)
The SOP is the core access control rule in browsers. It restricts how scripts or active content (e.g. JavaScript) interact with different resources to prevent Cross-Site Scripting (XSS) attacks. Under SOP, JavaScript or other active content on a web page is only allowed to communicate with the IP address (or web domain) it originally came from. This means that a script loaded from one website cannot access data or interact with a different website.
Sandboxing
Sandboxing in the context of browsers, the JavaScript (or other active content) is executed within a browser sandbox. The sandbox ensures that the script cannot alter the host system or access resources outside of what it is allowed.
For example, Google Chrome runs each tab in a sandbox environment. Each tab, and in some cases each extension, is run in its own process. This means that even if a malicious script compromises one tab, it cannot directly affect other tabs, extensions, or the underlying system.
Hardware access control
Memory protection - segmentation
CPUs help keep processes’ memory allocations separate using segment addressing. If a process tries to access memory outside its address space, a segmentation fault occurs, and the processes is forced to termination to prevent it from corrupting other processes and the operating system.
Privileged execution
CPUs have layered modes (rings) to support the OS, with different privilege classes. RAM has even separate registers with different privilege classes.
Isolated cryptographic components
Keys are stored in hardware, like Intel’s Trusted Platform Module (TPM), which provides secure key storage and usage.
Intel processor example
The Intel 80286 has segment addressing and rings. Modern Intel CPUs have nine rings:
0-3 for normal code, under which is a further set of rings 0-3 Virtual machine Manager (VMM) root made for hypervisor, and System Management Mode (SMM) for BIOS.
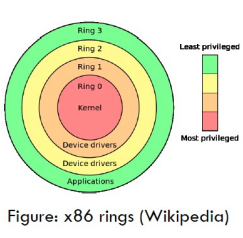 Code runs in one of the available CPU modes, called rings. CPUs enforce access control from higher privileged rings to lower. Process running in a higher ring cannot directly interact with process in lower.
Principle of least privilege suggests that all code should run only with minimal required privilege, never more. Number of ways to communicate with the kernel should be limited to required minimum.
Code runs in one of the available CPU modes, called rings. CPUs enforce access control from higher privileged rings to lower. Process running in a higher ring cannot directly interact with process in lower.
Principle of least privilege suggests that all code should run only with minimal required privilege, never more. Number of ways to communicate with the kernel should be limited to required minimum.
ARM processor example
ARM processors are most used in phones, tablets, and IoT devices. ARM-based design have their hardware protection extensively customised. ARM latest offered CHERI (Capability Hardware Enhanced RISK Instructions) helps multiple sandboxes run in the same process, and provide fine-grained spatial memory safety at a hardware level (potentially stop the day-zero exploits).
Back to parent page: Cyber Security and Security Engineering