A Message Authentication Code or MAC is a cryptographic checksum that is used to verify the integrity and authenticity of a message. Although MAC usually leverage hash functions, it is different from a simple checksum or hash; a MAC uses a symmetric secret key as part of its computation, which provides authentication by allowing the recipient to verify that the message came form the expected sender.
- Integrity
- When a sender computes an HMAC for a message, the HMAC is a cryptographic hash of the message combined with the secret key
- When the receiver gets the message and its HMAC, they can recompute the HMAC using the same secret key and the received message
- The receiver computed HMAC is compared to received HMAC to confirm whether the message has been altered
- Authenticity
- MAC confirms message was sent by someone who possesses the secret key
How a MAC works
- MAC generation
- A MAC algorithm takes two inputs: a message and a secret key
- It produces a MAC value (also called a tag)
- This process can be described as
- MAC verification
- Upon receiving the message and its accompanying MAC value, the recipient uses the same MAC algorithm with the same shared secret key to compute the MAC value of the received message
- The computed MAC value is compared to the received MAC value
- If the two MAC value matched, the message is considered authentic and unaltered
Hash-Based MAC (HMAC)
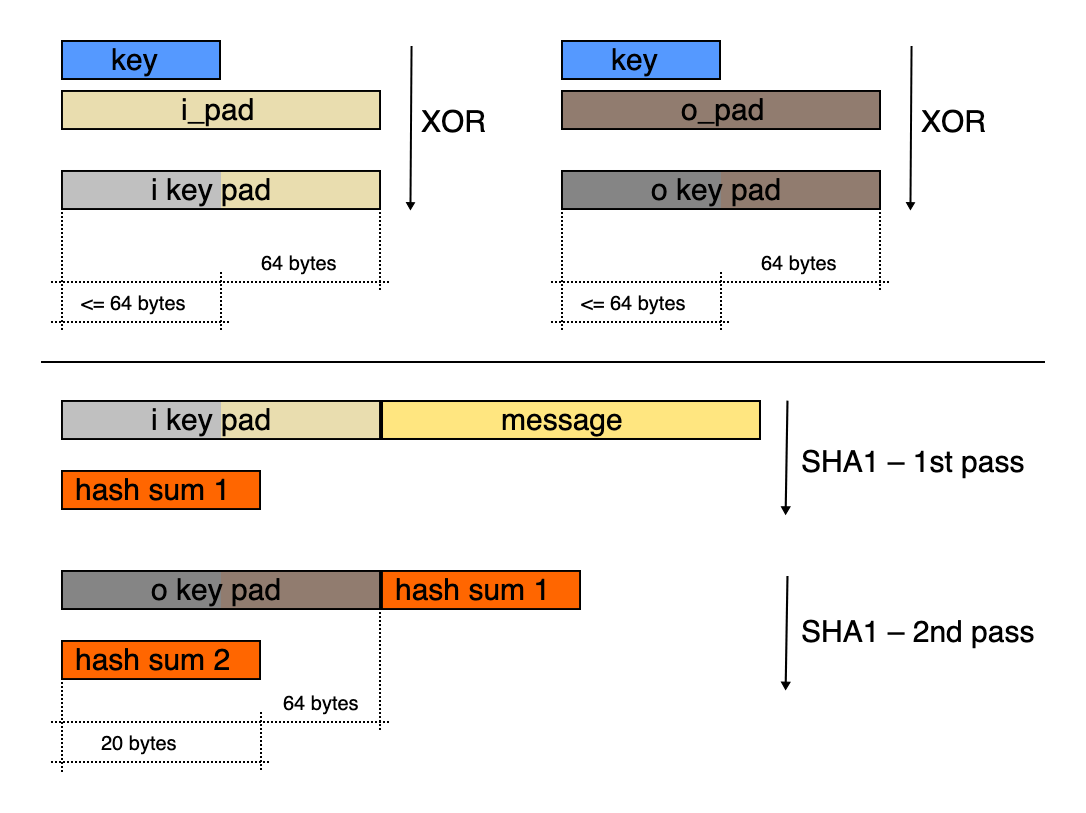
Hash-based Message Authentication Code (HMAC) is a construction algorithm used to generate MAC from cryptographic hash functions. The input to the HMAC algorithm is also secrete key and the message. The HMAC algorithm combines the secrete key and the message using a nested hash function to generate a hash value for a given message, which is the MAC.
Double hashing
The use of nested hash function in HMAC enhances the security. The hash functions uses padding to make the hash blocks to be compatible with the hash algorithm. In HMAC, two fixed sized blocked, called the inner pad () and outer pad (), are created.
The double hashing compute the hash of the concatenation ( ) of the and the message:
Then, compute the hash of the concatenation of the and the result of the inner hash:
Resistance to hash extension attack
Double hashing and secret key mechanism prevents attackers from being able to add additional data to the message (see Hash Extension Attack) and predict the new HMAC without the secret key.
Back to parent page: Network Security and Cryptography
Cyber_Security Network_Security INFO2222 MAC Authentication Integrity