Stream ciphers and block ciphers are two fundamental methods used for symmetric encryption, they both transform plaintext into cipher-text, but each with its own characteristics and use cases. The main difference between two methods is a block cipher converts the plain text into cipher text by taking plain text’s block at a time. While stream cipher converts the plain text into cipher text by taking 1 byte of plain text at a time.
Confusion and diffusion
Both confusion and diffusion are crucial properties that ensure the security of symmetric ciphers. They make it more difficult for attackers to exploit statistical relationship between plaintext and cipher text.
- Confusion
- Confusion refers to making the relationship between the cipher text and the encryption key as complex as possible.
- Diffusion
- Diffusion refers making each plaintext bit affects as many cipher text bits as possible. The goal is to ensure that any change in the plaintext effects many parts of the cipher text.
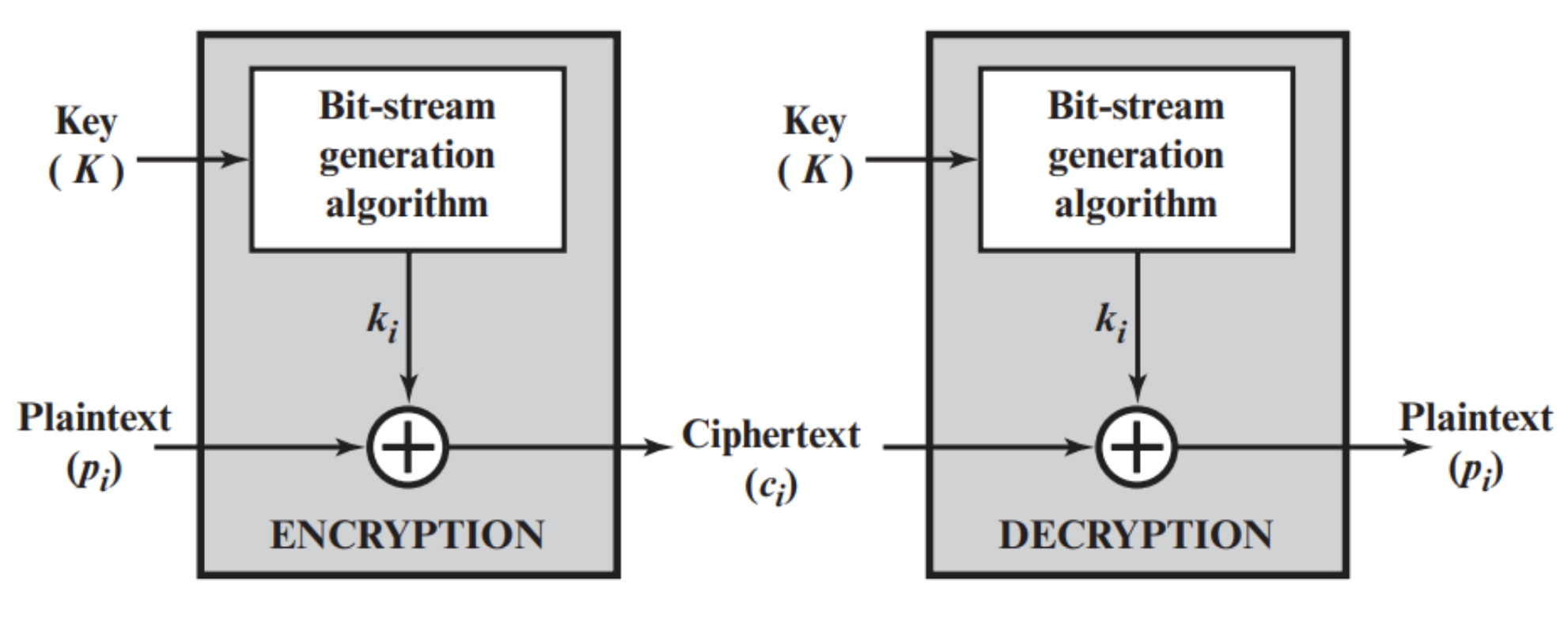
Stream cipher
Encrypts plaintext one bit or one byte (8 bits) at a time, continuously producing a stream of cipher text. Stream cipher don’t mix plaint text and key bits, it generate pseudorandom bits from the key and mix the plaintext and the generated key stream using a bitwise operation (typically XOR). The decryption is reversed by XORing the cipher-text with the same key.
Due to bit-by-bit encryption nature, stream cipher does not achieve strong diffusion compared to block cipher. Instead, the security of stream cipher mainly relies on the confusion, which the key stream should be statistically random and difficult to guess.
Block cipher
Encrypts fixed-size blocks of plaintext (e.g. 64 or 128 bits) at once. The plaintext is divided into blocks, and each block mixed with key bits to produce chunks of cipher text of the same size.
- Block size The size of the blocks influences the ease with which attackers may decrypt the cipher text. If the blocks are too small, there is less data for attackers to sift through and decode. On the other hand, if the blocks are too large, encryption and decryption process may becomes less efficient, especially when handling large volumes of data. Most block cipher, like AES, use block sizes of 128 bits or other similar sizes that also divisible by eight. This size strikes a balance between security and efficiency.
- Padding It is unlikely the total data to be encrypted will be perfectly divisible by the block size. To ensure that each block is of equal size, a method called padding is used. This involves adding redundant bytes to the last block to make it complete. PKCS#7 (Public Key Cryptography Standards #7) and ISO/IEC 7816-4 padding. These schemes add bytes to the plaintext.
Modes of block cipher
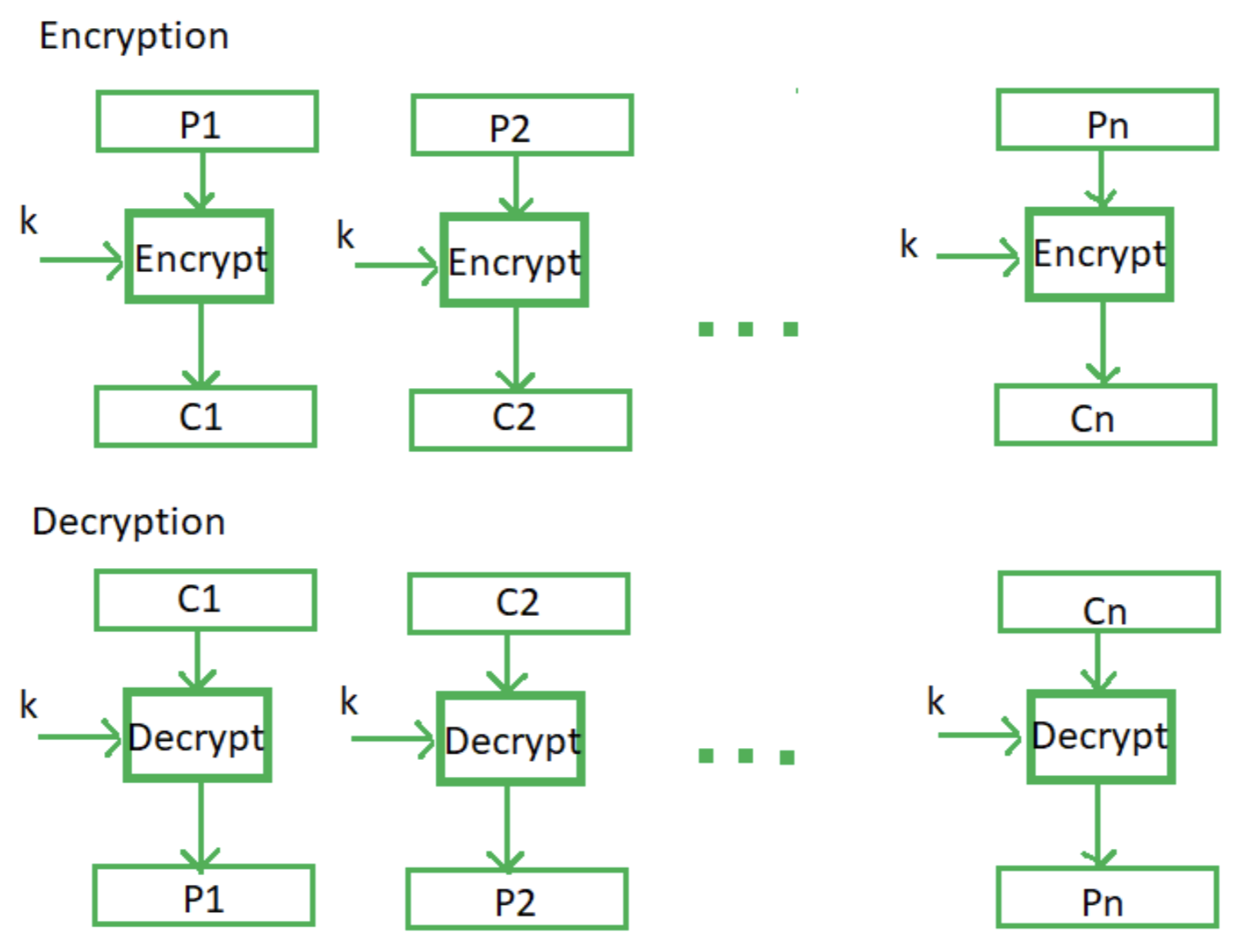
Electronic Code Book (ECB) mode
ECB is the easiest block cipher mode of functioning. Each block of plain text is encrypted independently of other blocks. The plain text is divided into fixed-size blocks (128bits for AES). Each plain text block is directly encrypted using the same key to produce a corresponding cipher text independently.
- Parallel encryption
- ECB allows for parallel encryption, as each block is processed independently of the others. This means that the encryption of one block does not depend on the results of previous block.
- Deterministic
- The encryption process is deterministic, meaning that the same plaintext block will always result in the same cipher text block when encrypted with the same key.
- Vulnerabilities
- Despite its simplicity, identical plaintext blocks will produce identical cipher text blocks using the same encryption key, one change in the plaintext won’t affect many parts of the cipher text since each block is independent. This lack of diffusion makes it easier for attackers to perform cryptographic analysis.
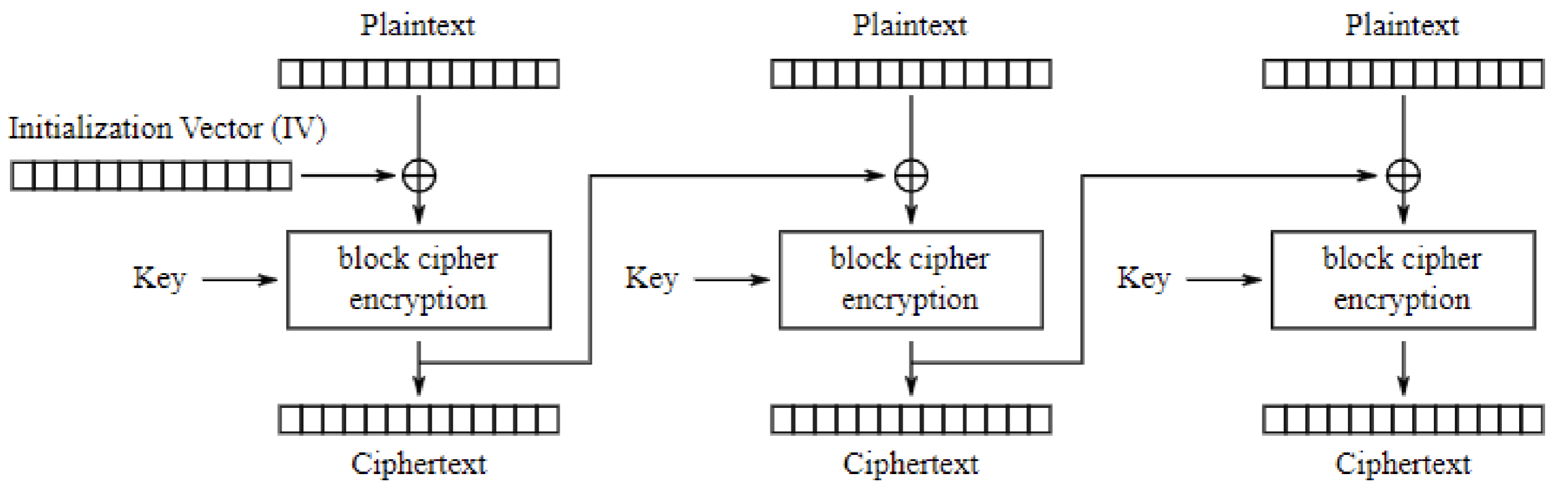
Cipher Block Chaining (CBC)
CBC is an advancement made on ECB, it resolved the some security vulnerability in ECB. In CBC each plaintext block is XORed with the previous cipher text block before encryption, introduces a chaining dependencies between blocks and providing better diffusion.
- Chaining
- Plaintext blocks of input get “chained” to previous output blocks of ciphertext.
- Drawback
- The error in transmission gets propagated to few further block due to the chaining effect.
Feistel cipher
Feistel cipher is a common structure used in block ciphers like DES, Blowfish, and others. It divides the data blocks into two halves and processes them in multiple rounds. Each round follows the same basic structure.
The detailed working of Feistel function will be discussed in latter DES.
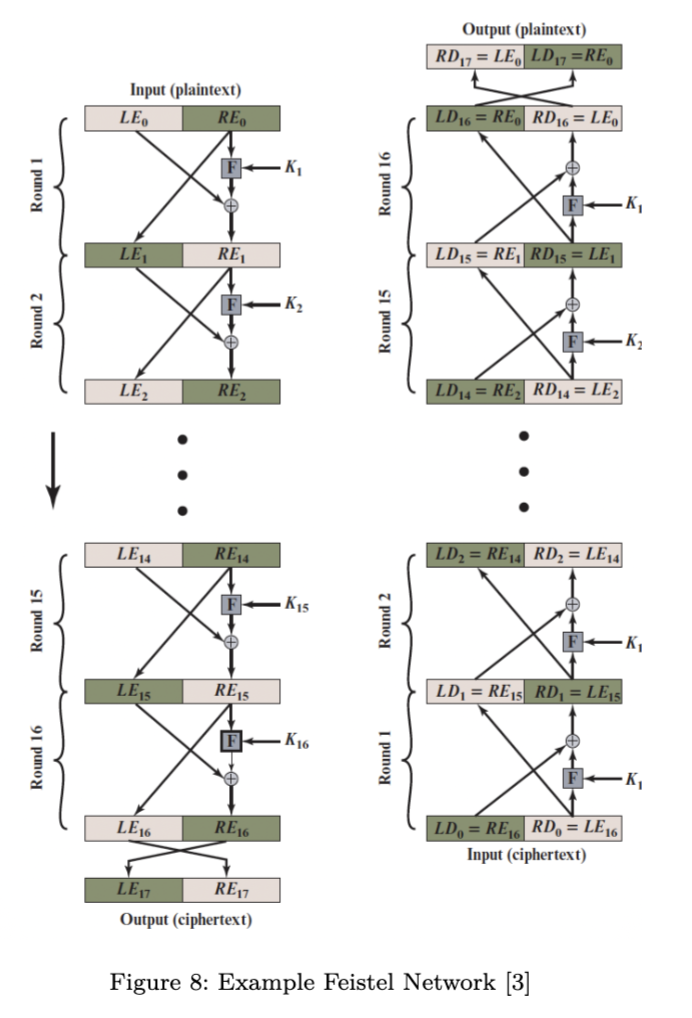
- Splitting the data Given a block of data , split it into two halves: and
- Round operations (for each round ) The right-hand side half goes through a keyed function , and the output is XORed with the left-hand side. Each round the takes a different key generated from a given key.
Data Encryption Standard (DES)
DES encryption algorithm, uses a key that, in each round, is transformed into a sub-key derived from the actual key (round key). The algorithm includes a total of eight S-boxes, with the outputs from these S-boxes being sent through one P-box to ensure good enough diffusion across the the S-boxes in the subsequent round. It is important to note that the 16 rounds utilised in this process are necessary to achieve the desired level of security. The algorithm employs a Feistel structure between rounds. As we discussed later, DES no longer considered secure.
S-boxes
S-boxes or substitution boxes are basically look-up tables. They take a block of input bits and map them to a different block of output bits. Each S-box has carefully chosen mapping to ensure security by scrambling data in a complex, non-linear way. For DES to work properly, the decryption process must be possible. This is ensured in two ways:
- Either S-boxes themselves are invertible, meaning there is a reverse mapping from output to input.
- Or, the entire arrangement of S-boxes within the cipher structure is designed in such a way that the cipher as a whole is invertible, even if individual S-boxes are not.
Diffusion property One of the key goals of the S-boxes is to achieve diffusion. This means that changing just one bit in the input to an S-box will, on average, result in half of the bits in the output being flipped.
DES is no longer secure While DES was considered secure when it was introduced, its key length (56 bits) is now too short, making it vulnerable to brute-force attacks. The more modern Advanced Encryption Standard (AES) also uses S-boxes but in a different manner, with larger and more complex structures.
Example S-box from DES
The below is an example of narrowing down S-box selects its 4-bit output based on a 6-bit input string.
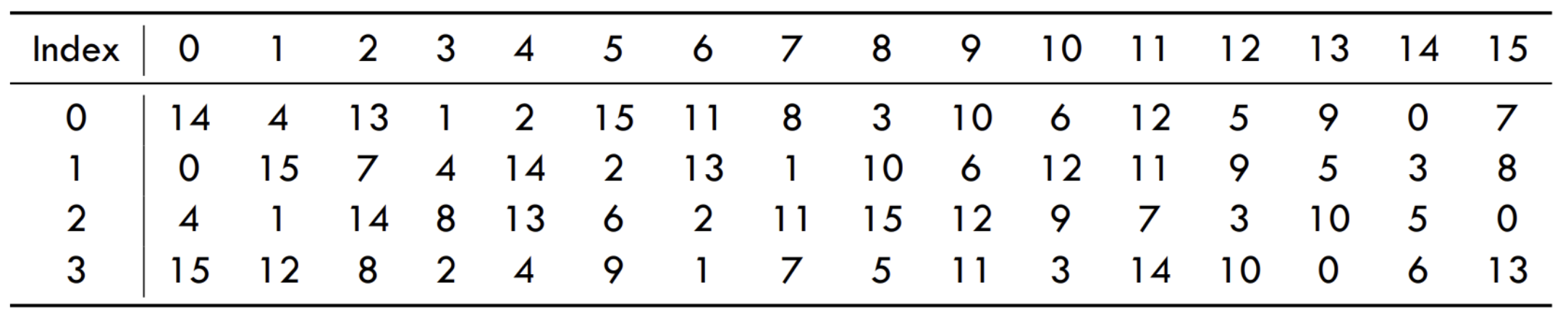 Given the input string , which is a 6-bit binary value, the S-box uses the following method to map it to a specific output.
Given the input string , which is a 6-bit binary value, the S-box uses the following method to map it to a specific output.
- Row selection ( and ) The first bit () and the last bit () are used together to determine the row in the S-box table. These two bits form a 2-bit number that can take values from 0 to 3 (i.e., 00, 01, 10, or 11), representing 4 possible row.
- Column selection () The middle four bits ( and ) are used to determine the column in the S-box table. These bits form a 4-bit number, which can take values from 0 to 15 (i.e., 0000 to 1111), representing 16 possible columns.
Example Input = =
Row: () = = Column: = =
Now we obtained the row index 3, and column index 11. Which corresponds to value 14. Output: = =
Example P-box from DES
P-box or permutation box is responsible for transposition or rearranging bits. Unlike S-boxes, which substitute bits, P-boxes only change the order of bits. P-boxes are often used in conjunction with S-boxes to create a chain where the output from S-boxes is passed through a P-box before being def into subsequent S-boxes. It ensures effective diffusion throughout the encryption process.
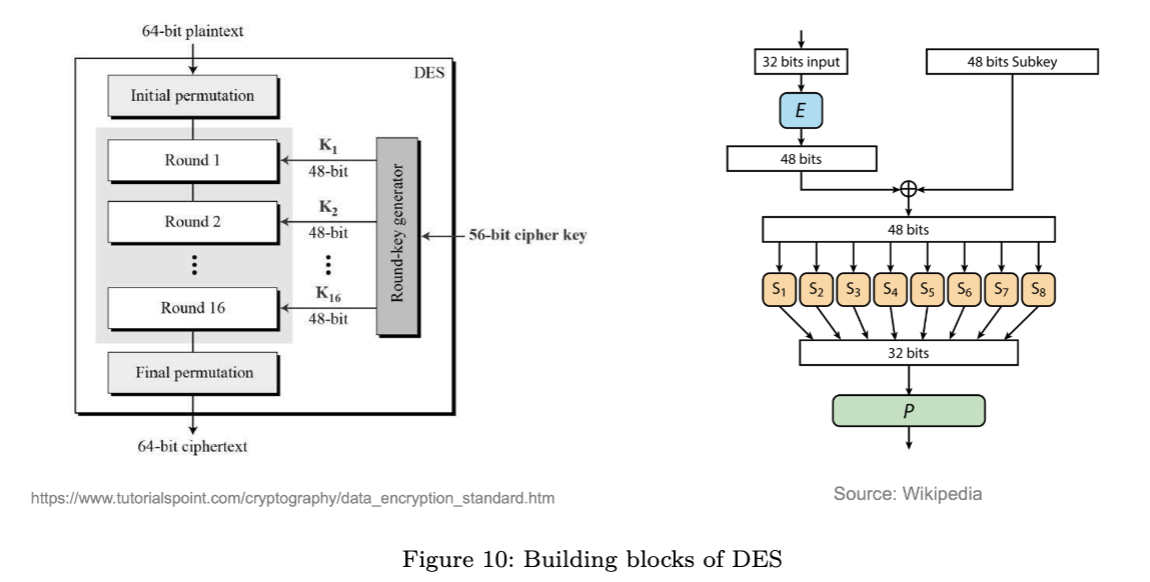 DES accepts data blocks of 64-bits, and its key size is 56-bits. The round-key generator generates 16 48-bit round keys to use in the 16 rounds.
The diagram on the right represents the Feistel arrangement (function F) inside each round.
Inside one round, the 64-bits input is split into two halves, left hand and right hand, 32 bits each. The right-hand side goes through the function F. The first 32 bits are expanded to 48 bits using the expansion box so that it is same size as the round key. Next, the expanded output is XORed with the round key and resulting 48 bits intermediate output is sent to 8 S-boxes, each S-box accepts 6-bit input. Each S-box (narrowing down) outputs 4 bits, so that 8 S-boxes results in 32 bits, making that output suitable for the next round. This process repeats 16 times.
DES accepts data blocks of 64-bits, and its key size is 56-bits. The round-key generator generates 16 48-bit round keys to use in the 16 rounds.
The diagram on the right represents the Feistel arrangement (function F) inside each round.
Inside one round, the 64-bits input is split into two halves, left hand and right hand, 32 bits each. The right-hand side goes through the function F. The first 32 bits are expanded to 48 bits using the expansion box so that it is same size as the round key. Next, the expanded output is XORed with the round key and resulting 48 bits intermediate output is sent to 8 S-boxes, each S-box accepts 6-bit input. Each S-box (narrowing down) outputs 4 bits, so that 8 S-boxes results in 32 bits, making that output suitable for the next round. This process repeats 16 times.
3DES
Triple DES (3DES) is an extension of the DES designed to replace the DES and provide enhanced security. 3DES improves upon DES by applying the DES encryption process three times in a row using 2 or 3 keys.
Three keys version
- Encrypt using DES with the first key
- Decrypt using DES with the second key
- Encrypt again using DES with the third key
The results in an process is known as Encrypt-Decrypt-Encrypt (EDE). When using three distinct keys, providing a key length of 168 bits (56 bits per key * 3)
Two keys version
- Encrypt using DES with the first key
- Decrypt using DES with the second key
- Encrypt again using DES with the first key
This is known as 2-key 3DES. While this version is less secure than the three-key variant, it still significantly improves upon single DES. The effective key length is 112 bits (56 bits per key * 2).
Back to parent page: Network Security and Cryptography
Cyber_Security Network_Security INFO2222 Confusion Diffusion Block_Cipher Stream_Cipher ECB CBC ESEC3616