RSA is a asymmetric key encryption algorithm developed in 1977 by Ron Rivest, Adi Shamir, and Len Adleman. The name RSA is taken from their surname initials. The RSA is still popular as of now (2024) and could be replaced by post-quantum encryption algorithms in the future with the emerging of quantum computing.
RSA key generation
- Two prime numbers and Come up with and , where and are extremely large prime numbers (greater than 2048 bits) and they cannot be to close to each other.
- Calculate The number is calculated as
- Calculate the Calculate the Euler’s phi of . Where .
- Choose the encryption key (public key) The encryption key follows the conditions that The second condition suggests that has to be co-prime with , which means cannot share any factor of .
- Calculate the decryption key (private key) The is deterministic once and is obtained. The equation to calculate can be described as below. And it can be rearranged to:
- Public key
- Private key
After the key generation, all , , and have to be permanently deleted for prevent reconstruction. The number is a public information.
Encryption
Encryption by Bob with Alice’s public key. Plaintext: Ciphertext:
Decryption
Decryption by Alice with Alice’s private key. Ciphertext: Plaintext:
Number mapping
The RSA algorithm can only encrypt numbers. Therefore, letters have to be mapped to numbers before they can be encrypted. The letter a maps to 1, and the letter b maps to 2…
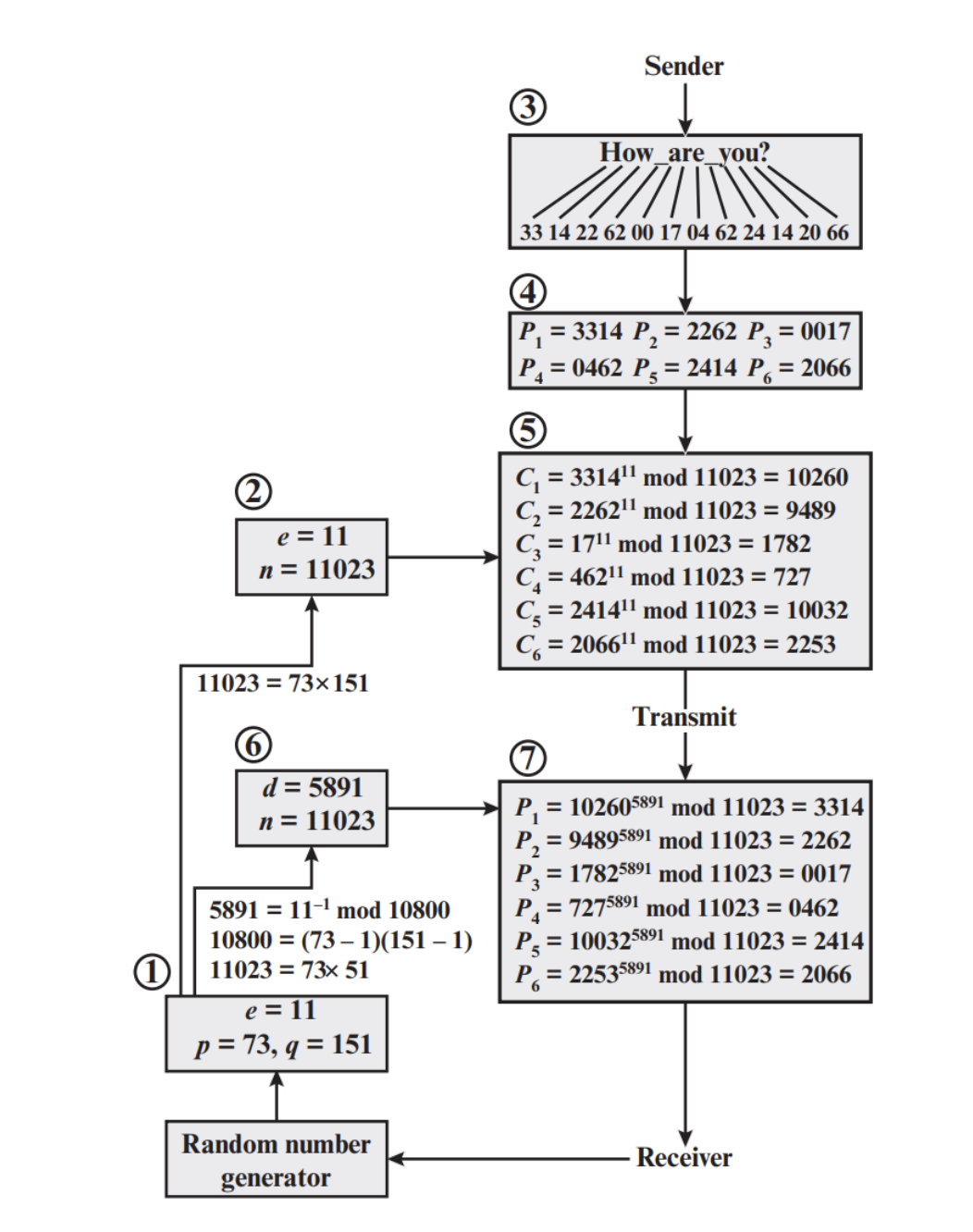
Security of RSA
The RSA algorithm make use of the trapdoor property. The security of RSA rests on
- Obtaining the root is computationally infeasible unless you know .
- Factoring is computationally infeasible for large primes.
If an attacker could factor into and , they could easily compute and use it to calculate from . However, if and are large and randomly chosen, factoring them is considered computationally infeasible with current technology.
To maintain the security of RSA
- and , must be very large (greater than 2048 bits)
- and , must not be too close together (allows forms fast factoring)
- Never implement RSA yourself and use in production
Attacks on RSA
- Brute force
- Trying all possible private keys
- Mathematical attacks
- Approaches to factoring the product of two primes
- Timing attacks
- Attacker monitors how long each RSA operation takes and use this information to infer bits of the private key, Using constant-time algorithms that perform computations in the same amount of time regardless of the input values
- Hardware fault-based attack
- Inducing hardware faults in the processor that is generating digital signatures.
- Chosen ciphertext attack
- The attacker choses a specific ciphertext and observe the corresponding decrypted plaintext. This allows them to exploit the structure of the RSA, especially RSA that is malleable or improperly implemented.
Malleability of RSA
RSA is not secure to use without padding
The malleability of RSA allows attacker to manipulate the encrypted messages without needing to know the actual contents of the original message. The malleability of RSA arises because of its mathematical structure. As the working out earlier, the RSA encryption can be described as: Where
- is the plaintext message
- is the public exponent
- is the modulus (product of two large prime numbers and )
- is the resulting ciphertext
Chosen Ciphertext Attack (CCA)
If an attacker intercepts a ciphertext and wants to generate a new ciphertext such that the decrypted plaintext is a known transformation of the original plaintext , they could exploit RSA’s malleability as follows: If the attacker multiplies the plaintext by a random factor , they get: When is deciphered by the receiver, the plaintext becomes . The receiver then ask the sender (attacker) that what does the plaintext mean? The attacker can take the plaintext and divide it by to obtain the original message .
Padding
The malleability of RSA is considered a weakness because it allows unauthorised manipulation of messages. To address this, secure implementations of RSA use padding schemes like OAEP (Optimal Asymmetric Encryption Padding) that adds more randomness on encryption and removes it on decryption.
Hybrid encryption
Almost all public-key encryption uses hybrid encryption in practice.
Problems with RSA
Public-key cryptography is slow
RSA replies on the exponentiation of large numbers, and performing arithmetic operations on large integers, which makes it computationally expensive compared to symmetric cryptographic algorithm like Advanced Encryption Standard (AES). RSA is 100-1000 times slower than AES.
Mapping numbers to characters
RSA works with numbers, so characters must be converted into numerical representation, this process has impact on the RSA performance. It involves encoding the text in a form that RSA can work with (mentioned in number mapping).
The use of hybrid encryption
Hybrid encryption combines the strengths of both asymmetric and symmetric encryption to overcome the limitations of RSA performance in continuous encryption. In hybrid encryption:
- Asymmetric encryption: Used to securely exchange a symmetric key.
- Symmetric encryption: Used to efficiently encrypt and decrypt actual data in communication.
Back to parent page: Network Security and Cryptography