Security framework
Security engineering uses security framework to design and access the security of a (distributed) system. Also, a framework will help assist investigations after a security incident. The security framework includes policies, mechanism, assurances, and incentives to maintain security. Each components are interconnected.
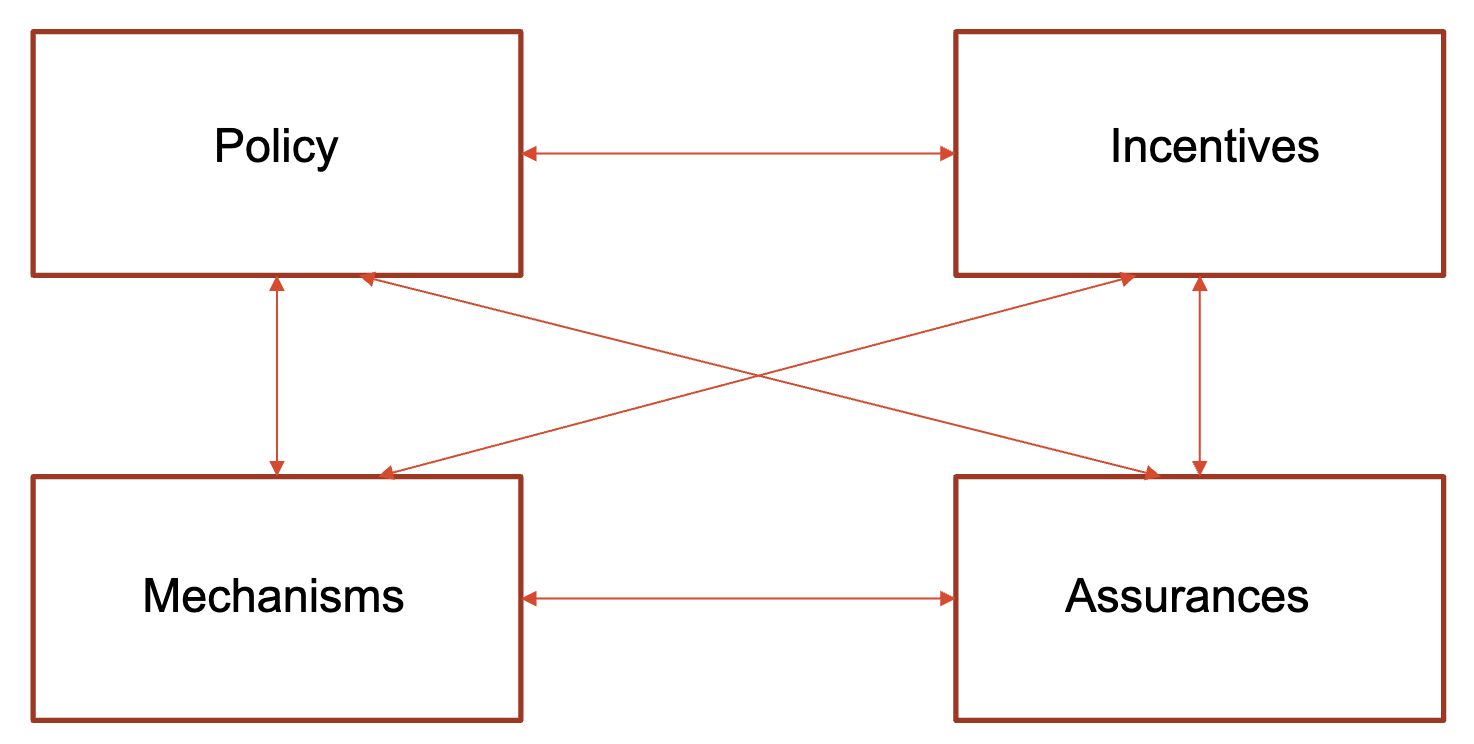 Security framework is closely related to security goals, which will be discussed later in this page. Security goals help articulate the policies within the framework. Mechanisms are then employed to achieve these goals, and assurances ensure their reliability. Understanding incentives helps prioritise these goals and mechanisms.
Security framework is closely related to security goals, which will be discussed later in this page. Security goals help articulate the policies within the framework. Mechanisms are then employed to achieve these goals, and assurances ensure their reliability. Understanding incentives helps prioritise these goals and mechanisms.
Policy
Policies define what it means to keep the system secure, such as ensuring business continuity and complying with regulations and standards. They are often set by the higher management.
Note
A policy do not define how to achieve or implemented, rather they define guide the implementation of security mechanisms and practices.
Some example policies are:
- “Customer data must be stored only within our data centres.”
- “Only authorised employees must be able to access the personal information of clients.”
Mechanism
A mechanism refers to the tools and methods used to implement policies. Security engineers must be aware and familiar with various mechanisms that are required to implement policies. Here are some key mechanisms:
- Encryption Ensures data confidentiality by converting information into a code to prevent unauthorised access.
- Tamper-resistant hardware Provide physical security to protect against unauthorised access.
- Cryptographic hashes Maintains data integrity by verifying that data has not been altered.
Assurance
Assurance refers to the confidence you can place in the effectiveness of security mechanisms and how well they work together. Security engineers must be able to conduct professional estimates of assurances given by commonly used security mechanisms.
Some examples about assurance are:
- How much time is required based on current computing capabilities to break RSA encryption?
- How much time is required to brute-force a 10-character password.
Incentive
Incentive refers to the motivation behind the actions of both those protecting system and those attacking it. Security costs money, understanding incentives allows us to understand the degree of security we need.
- Defenders’ motives The reasons why people guarding and maintaining the system.
- Attackers’ motives The reasons why attackers are driven to defeat a system. This can vary based on the type of attacker, such as state actors, cyber criminals, hacktivists.
Threat modelling The methodical process of understanding the possible threats and prioritising defence mechanisms is called “Threat Modelling”.
Security goals
Security goals are used to define the security polices, they are objectives that ensures the protection of the system. There are considerable overlap between some of the goals.
- Confidentiality (sometimes secrecy)
- Data/Message integrity
- Authenticity
- Authorisation
- Accountability
- Non-repudiation
- Deniability
- Availability
- Privacy
Confidentiality and secrecy
Confidentiality refers to the mechanisms that limit who can access data in plaintext form. It is the goal of protecting the secret content of a message or data, commonly by encryption.
Data/message integrity
Integrity refers to the of a mechanism to allow a verifier to check whether a message has been modified in transit or data has been changed since the last honest write.
- Verification Mechanisms allow a verifier to check if data has been modified.
- Detection Detect changes even if preventing them is challenging.
- Tamper-evident Ensures that any unauthorised modifications are noticeable.
- Not tampering-resistant Unlike tampering resistance, which aims to withstand modifications, integrity focuses on detection.
Authenticity
Refers to the effect of allowing a verifier to determine the originator of a message or data item. It ensures that the information comes from a trusted source and has not been tampered with. In cryptographic protocol, the term also implies integrity and freshness.
- Integrity When trying to authenticate, we need integrity.
- Freshness We need to proof that the other party is active in the process and not someone else replaying recorded messages.
It is not the same as authentication, which is the process of identifying a party we are communicating with.
Authorisation
Refers to the effect that a verifier can determine whether an entity is allowed to execute some action or access some data. Authorisation often makes use of authentication but does not imply it. For example, when you entre a cinema, you only need to show authorisation, not who you are.
Authorisation is closely linked to access control and accountability.
Accountability
Refers to the effect that a verifier can determine which entity (or which category of authorised entities) is responsible for a certain action. Accountability needs some form of logging, the logs have to be auditable (the verifier can access and rely on the logs), and the logs needs to be protected. It implies:
- One can trace the actions of an entity through the system
- Authorisation and access control
It may imply authentication, and it is closely related to non-repudiation.
Non-repudiation
Means the the entity who has caused an action cannot successfully deny responsibility.
- Legal concept At its core, non-repudiation is a legal principle that prevents entities from denying actions such as sending or receiving a transaction.
- Cryptographic proof In cryptography, non-repudiation involves ensuring authenticity and integrity, often through secure timestamping of actions.
- Supported by accountability Accountability mechanisms, such as logging and auditing, support non-repudiation by providing evidence of actions taken.
Deniability
Deniability is the capability to successfully reject the notion of being responsible for some action. It is the opposite of non-repudiation in many ways.
Availability
Refers to the system’s capability of providing its services when needed, even during an attack, error, or mishap. Achieving availability is challenging as attackers often have a huge attack surface to choose from.
Privacy
Implies an entity’s right to determine what information relating to themselves they want to release or hide. Privacy has different aspects:
- Privacy of static data (released data sets)
- Privacy of dynamic data (DB queries)
- Privacy when moving through the network
Security policy model
A security policy model is a highly precise and concise statement about the protection properties of a system. It formalises security policy in a more structured, often mathematical or logical form, that can derive the design and engineering of the system. Security policy model bridges the gap between high-level goals in the security policy and the actual implementation.
When analysing a system’s security, one often follows the other:
- Analyse incentives and create a threat model that describes the attacker’s motivations and capabilities.
- Analyse security policy that describes the goals to be achieved.
- Analyse security mechanisms to implement the security policy.
Bell-LaPadula model
The Bell-LaPadula model is a security policy model used to enforce access control, primarily focusing on data confidentiality. It ensures that classified information is not accessed by unauthorised users, emphasising “no read up, no write down” rules.
Two forms of MAC
It includes the simple security property (no read up), and the * (Star) property (no write down).
- Simple security property
- No principal (user) may read data at a higher security level than their own clearance.
- * (Star) Security property
- No principal (user) may write data to a lower security level than their own clearance.
The * property is crucial, it ensures that users at low security level writes a program to exfiltrate data.
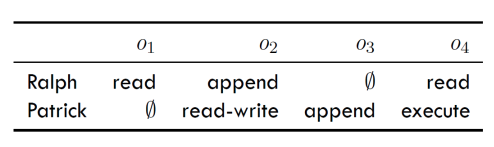
One DAC
Bell_LaPadula has one DAC, external entity defines the access of subjects to objects in a matrix.
Innovations and criticisms
- Innovation
- Lends itself well to formal analysis.
- Combine DAC and MAC.
- Criticism
- It relies on one omnipotent Trusted Principal, which raises concerns about securing that entity.
- The model is designed with confidentiality in mind, not integrity.
- It does not consider convert channels, such as encoding data in CPU load.
- A system composed of two Bell-LaPadula secure system is not necessarily secure under Bell-LaPadula.
Biba model
Biba model is a security policy model focused on integrity (improper modification to data) rather than confidentiality. You can think of it as a reserve of Bell-LaPadula.
- Read up (no read down): principle may only read data at own level or higher.
- This prevents a user from reading information from a lower integrity level, ensuring they don’t rely on potentially corrupted or untrusted data.
- Write down (no write up): principle that may only write data at own level or lower.
- This ensures that a higher-integrity process cannot be influenced by lower-integrity data but can provide input to lower-integrity systems.
- Invocation property: principal cannot obtain any access to objects at higher level (only own and lower).
For example, aircraft in-flight entertainment system can read data from avionics (e.g. airspeed), but cannot affect it.
Use of models
Pure Bell-LaPadula implementations (or any other model) are rare. Variants of Biba, are more common (e.g. Windows Vista, SELinux).
Security principles
- Economy of mechanism
- Fail-safe defaults
- Complete mediation
- Open design
- Separation of privilege
- Least privilege
- Least common mechanism
- Psychological acceptability
- Isolation
- Encapsulation
- Modularity
- Layering
- Least astonishment
Security attack
Any action that compromises the security of information owned by an organisation.
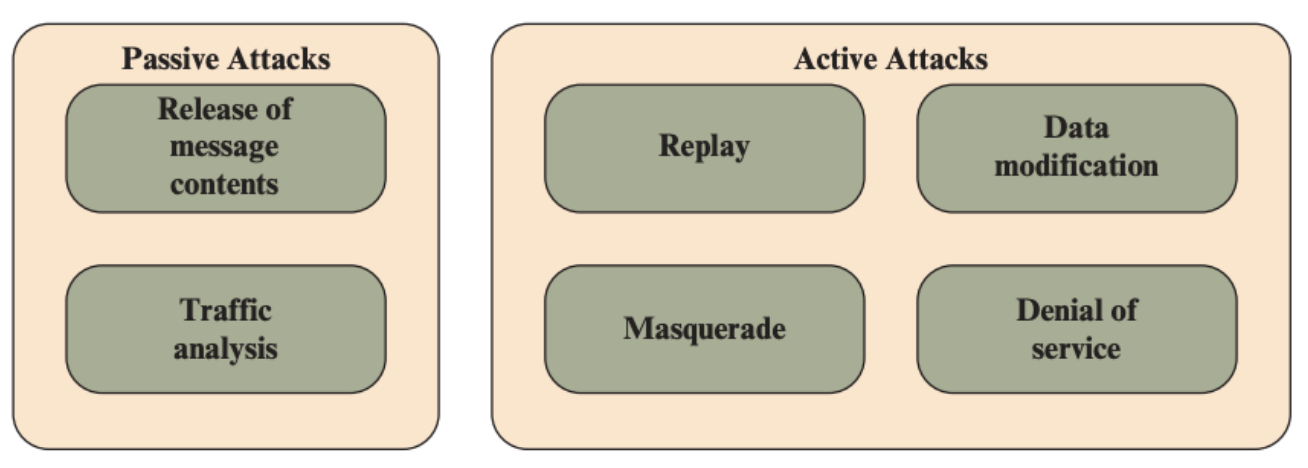
- Passive attack Passive attacks are in the nature of eavesdropping on, or monitoring of, transmissions. The goal of the attacker is to obtain information that is being transmitted.
- Active attacks Involves some modification of the data stream or the creation of false stream and can be subdivided into four categories: replay, masquerade, modification of message, and DoS.
Attack vector
An attack vector is a specific method or pathway through which a hacker or malicious actor gains unauthorised access to a computer or network system.
Examples:
- Phishing Using fraudulent emails or messages that appear to be from a trusted source to trick individuals into revealing sensitive information or clicking on malicious links.
- Malware Software designed to harm or exploit any programmable device, service, or network. Attackers can introduce malware through email attachments, software downloads, or operating system vulnerabilities.
- Person-in-the-middle attacks Interception of the communication between two parties to steal or manipulate the data being exchanged.
Attack surface
Consist of the reachable and exploitable vulnerabilities in a system. In another word, the sum of all points on a system where attackers can attempt to gain unauthorised access. Can be categorised as follows:
- Network attack surface
- Software attack surface
- Human attacker surface
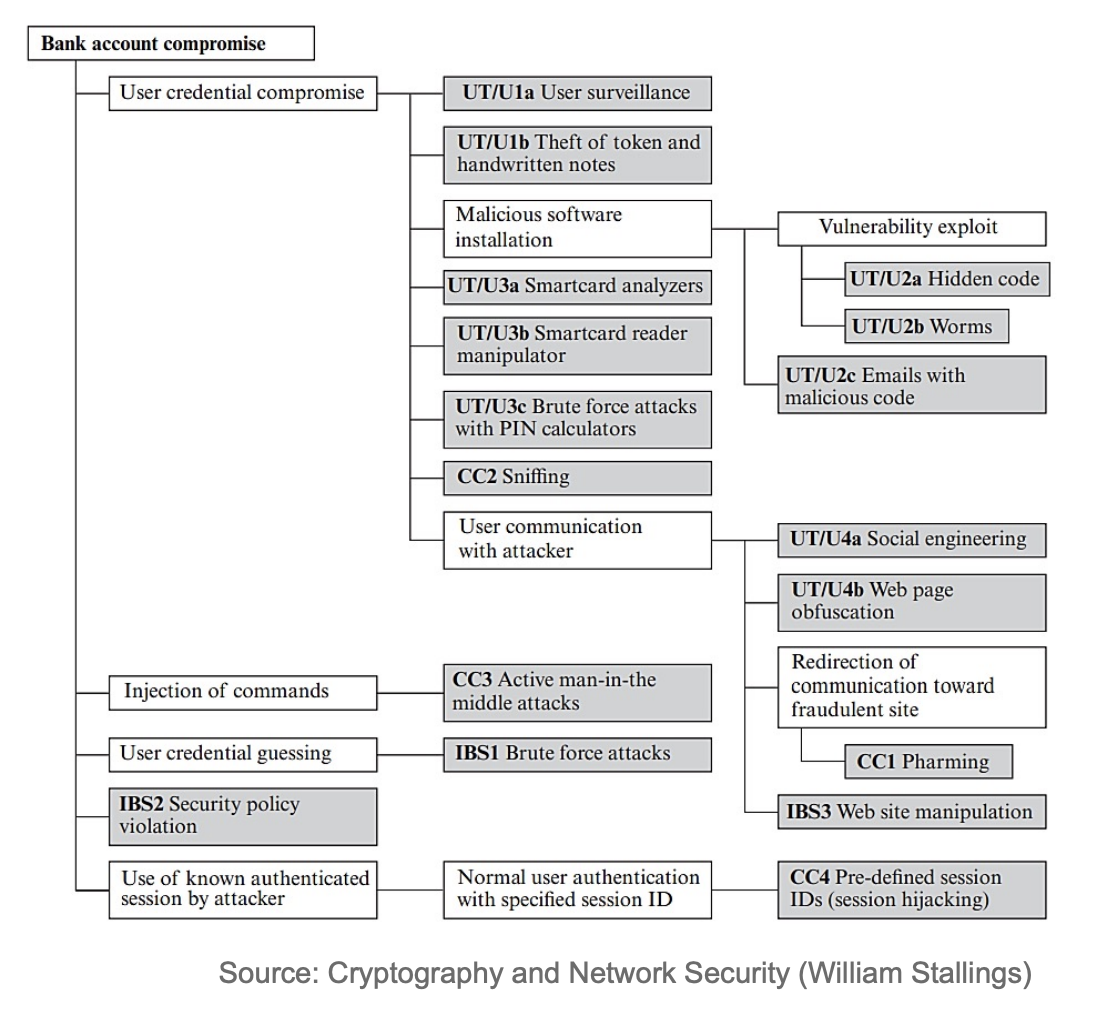
Attack tree
An attack tree is a branching, hierarchical data structure that represents a set of potential techniques for exploiting security vulnerabilities.
Back to parent page: Cyber Security and Security Engineering
Cyber_Security Security_Framework Security_Policy_Model Security_Principle